There are many different types of attacks in cyber security — and network security teams must worry about all of them. While no organization can protect themselves against every type of threat, a company is expected to demonstrate due diligence in protecting against the most common forms of cyber-attacks.
The bulk of cyber-attacks are no longer carried out by a lone hacker in their basement. Today, highly organized and well-financed organizations treat cyber security attacks as a business, and they have the means to launch attacks on organizations of every size and industry. With the cost of cybercrime expected to reach $10.5 trillion by 2025, the ability to protect your users and enterprise systems from both external attacks and insider threats is imperative. In fact, it has become a competitive advantage for some companies.
This article describes the 12 most common cyber threats today and provides cyber-attack examples.
Both denial-of-service and distributed denial-of-service attacks are malicious attempts to make a server, service or network resource unavailable to its intended users. The difference is while a DoS attack comes from a single source, a DDoS attack is implemented from multiple sources, sometimes globally distributed.
DoS and DDoS attacks do not seek unauthorized access; rather, they focus on preventing genuine traffic from accessing its intended destination by overwhelming the target with garbage traffic that consumes the available bandwidth of that host. The underlying reasons might range from targeting a competitor’s website to extorting the victim business to pay the adversaries to stop the attack. Another purpose of a DoS or DDoS attack can be to take a system offline as a distraction so that a different kind of attack can be launched.
The amount of traffic generated by these attacks can be substantial. In 2018, GitHub withstood a DDoS attack for 20 minutes in which it was pummeled by 1.3 terabits per second (Tbsp) of traffic, which was the largest DDoS attack to date. In 2021, however, Microsoft suffered an attack of 3.4 Tbps.
Cyber criminals use different types of DoS and DDoS attack methods, which require different defense strategies. Here are the most common ones include the following:
Botnets can be difficult to trace because the machines being used are often in many different geographic locations. One way to curtail botnet attacks is to configure your firewalls to block traffic from countries or IP ranges that your organization does not serve. Other measures include rate limiting, traffic filtering, 24/7 monitoring and implementing web application firewalls (WAFs).
One countermeasure to thwart these types of attacks is to place servers behind a firewall configured to stop inbound SYN packets. Another is to increase the size of the connection queue and decrease the timeout duration for open connections.
While many vendors supply patches that protect their systems from such attacks, you can further protect against them by disabling SMBv2 and block ports 139 and 445.
One way to protect your devices from this attack is to disable IP-directed broadcasts on your routers; this will prevent the ICMP echo broadcast request at the network devices. Another option is to configure the endpoint systems to keep them from responding to ICMP packets from broadcast addresses.
Ping of death attacks can be blocked by using a firewall that will check fragmented IP packets for maximum size.
Download Free Guide:In a MitM attack, a hacker secretly intercepts and potentially alters the communication between two parties, while tricking both parties into believing they’re communicating directly with each other. Goals can include stealing information or injecting malicious data.
For example, an attacker might set up a rogue wireless access point (WAP) that spoofs a legitimate WAP by using the same or a similar network name (SSID). Unsuspecting users connect to this rogue WAP thinking it’s a trusted network, and then all their wireless data traffic passes through the rogue access point. This enables the attacker to intercept, inspect and modify the data.
Two of the most common types of MitMs are:

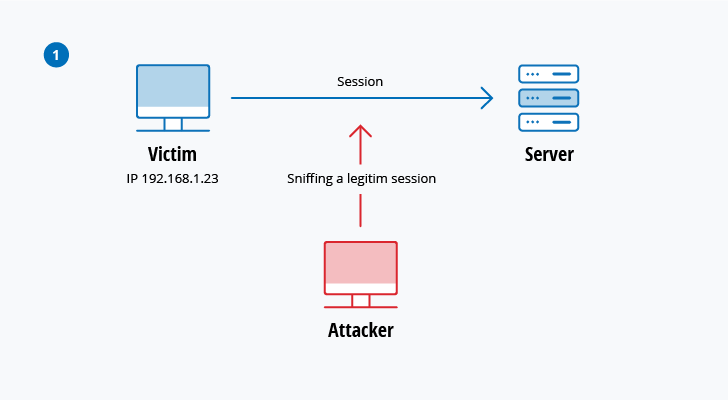
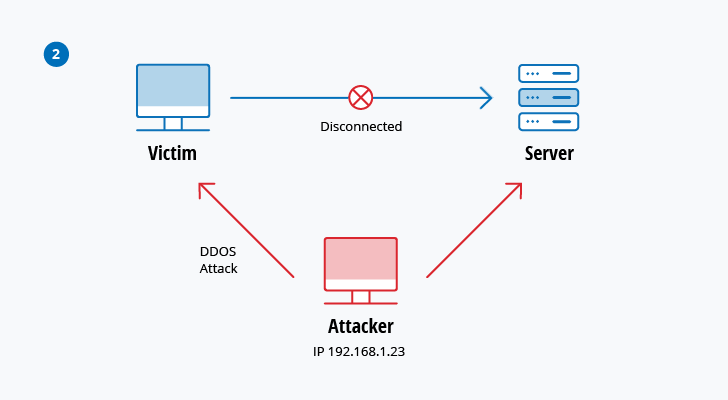
The diagram below shows how the attacker could then launch a DoS attack to keep the victim’s system offline. and then connect with the server after hijacking the session.
While there is no single technology or configuration to prevent all MitM attacks, there are some security measures organizations and individuals can take to protect themselves against these types of attacks. Best practices include the following:
Phishing attacks combine social engineering and technical trickery to send emails that appear to be from trusted sources, often to either glean personal information like login credentials or to deploy ransomware. Spear phishing is a targeted form of phishing attack in which hackers gather detailed information about a specific individual or organization in order to customize their messages and make the scam more convincing.
The email might urge the user to open an attachment that purports to be innocent but is actually infected with malware. Or it might try to deceive the recipient into visiting a fake website designed to look like their financial institution in order to capture their login credential, or prompt them to download malicious software onto their computer. Phishing attacks are so prominent that 9 in 10 enterprises fell victim to some type of phishing attack in 2022.
One way that hackers make their phishing emails look legitimate is email spoofing — making the information in the “From” section of the email appear as if the email is coming from someone you know, such as your management or your partner company. For example, in 2016, attackers spoofed the email account of the newly appointed CEO of Mattel Corporation in a spear phishing email to the CFO, who wired more than $3 million to a bank account in China. (Luckily, the company was able to reclaim the money.)
Because email remains the primary vector for cyberattacks, a robust email security solution is essential. However, no tool is foolproof, so the following supplementary are wise:
Drive-by cyberattacks exploit vulnerabilities in websites to redirect users to malicious sites and discreetly download malware onto their devices. These steps occur without any further action from the user, or even their knowledge.
In other words, merely visiting a website can get your device infected. As an example, an estimated 11,000 WordPress sites were found to be infected with an elusive strain of malware in 2023.
These attacks take advantage of outdated software or unpatched systems, so keep your operating systems and web browsers updated. In addition, users should stick to sites they normally use, and reduce the attack surface of their devices by removing unnecessary applications and browser plugins.
Password attacks aim to gain unauthorized access to sensitive information and systems by compromising user passwords. Here are a few of the main attack types:
Passwords remain the most used mechanism to authenticate users, but the reality is, passwords alone are no longer sufficient to protect online accounts. It’s essential to adopt multifactor authentication, which combines at least two of the following: something you know (like a password), something you possess (such as a cellphone or FIDO key), and something inherent to you (like a fingerprint).
Organizations should also establish policies that lock accounts after several unsuccessful login attempts. For optimal results, follow account lockout best practices.
In this form of password attack, cybercriminals use usernames and passwords leaked in prior data breaches to gain access to accounts. These attacks bank on the fact that many people reuse passwords across multiple sites. For example, a hacker may obtain the login credentials of 50,000 users from a breach at one website. When they use these credentials to try to access popular platforms like PayPal.com or major banks, it is likely that a small fraction of those attempts will be successful.
Databases of compromised credentials are actively traded on the dark web; in fact, more than 24 billion username/password combinations are estimated to be in circulation. For example, in 2022, attackers attempted to log in to Norton Password Manager using 925,000 stolen credentials; they successfully compromised an undisclosed number of customer accounts.
The best defense against credential stuffing attacks is to educate users to use a unique password for every online account they use, and to make doing so easy by providing a high-quality password management solution.
In addition, if possible, make each person’s username different from their email address. Organizations should also require MFA to render compromised credentials useless.
SQL injection attacks consistently rank near the top of OWASP’s top ten web application risks. These attacks exploit vulnerabilities in a website’s code to insert malicious SQL code into input fields or application queries. If a site doesn’t properly validate or sanitize user input, an attacker can trick the database into executing unintended SQL commands, enabling attackers to access sensitive information, bypass login credentials or even manipulate website content.
To defend against SQL injection attacks, ensure that all your SQL servers are updated and patched regularly, and employ the least-privilege model for database permissions. Prioritize the use of stored procedures and prepared statements (parameterized queries). You should also have a way to validate input data using a whitelist at the application level.
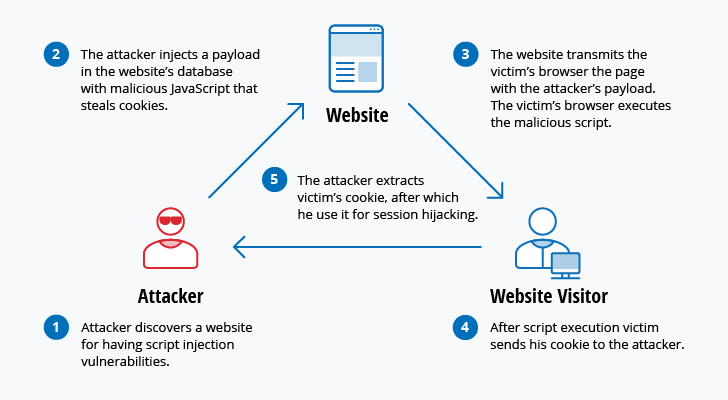
Cross site scripting attacks use third-party web resources to run scripts in the victim’s web browser or scriptable application. This can be instigated by injecting a payload with malicious JavaScript into a website’s database. When the victim requests a page from the website, the website transmits the page, with the attacker’s payload as part of the HTML body to the victim’s browser that executes the malicious script. For example, it might send the victim’s cookie to the attacker’s server, allowing the attacker to extract it and use it for session hijacking. Scripting XSS can be used to exploit additional vulnerabilities that enable an attacker to log keystrokes, capture screenshots, discover and collect network information, and remotely access and control the victim’s machine.
In 2022 alone, OWASP found more than 274,000 occurrences of some form of SQL injection and cross-site scripting being used. The typical cross-site scripting attack process is outlined below.
Defending against cross-site scripting (XSS) attacks requires a combination of robust coding practices and security tools. Important best practices include the following:
Malware is any form of malicious computer software device. Malware can be introduced to a system through various means, including email attachments, software downloads, USB sticks, malicious websites and legitimate websites that have been infected. Once a single system is infected, malware can propagate through the network to infect more network connected servers and devices. Malware can slow computer performance by consuming system resources.
Some of the most common types of malware today include the following:
The primary way to secure computers against malware is to use a modern endpoint security solution. Unlike traditional tools, which rely on signature-based malware identification, today’s advanced endpoint applications use heuristic techniques to detect anomalous activities.
Organizations can also implement firewalls that analyze and filter traffic to discover and block potentially harmful code before it infiltrates the network.
Ransomware is perhaps the biggest global cyber threat today. Ransomware cost the world more than $20 billion in 2021 and that figure is expected to grow to $261 billion by 2031.
Ransomware is malicious software that encrypts a victim’s data and systems to render them inaccessible. The attacker then demands a ransom from the victim, typically in cryptocurrency, for the decryption key to restore access. While federal law enforcement discourages paying these ransoms, businesses often do so to get their operations back online as quickly as possible. Ransomware gangs often also attempt to encrypt the organization’s backups so they cannot be used to restore systems and data.
Download Free Guide:As an additional form of extortion, many ransomware attackers will exfiltrate a company’s data before encrypting it and threaten to release or sell the data unless the ransom is paid. That way, even if an organization can restore their data themselves, they are forced to pay the ransom.
Ransomware attacks are challenging to defend against due to their increasing variety and sophistication. Indeed, there is no one way to prevent a ransomware attack. It requires a multi-layer security strategy that incorporates multiple security measures, including the following:
For additional advice on defending against ransomware attacks, check out these best practices and these 6 tips.
A zero-day attack exploits a software vulnerability that’s unknown to its vendor and the broader security community. Since there’s no prior knowledge of the vulnerability, there’s often no specific defense or patch in place when the attack occurs. This gives developers zero days to address the issue before it’s exploited.
Since zero-day attacks exploit uncharted vulnerabilities, key best practices like regular patching and configuration management provide little help. Instead, focus on a defense in depth cybersecurity posture that includes effective monitoring of your IT estate, threat intelligence, network segmentation, application whitelisting and anomaly detection .
Organizations are rapidly adopting multifactor authentication (MFA) not just for privileged access but for all users. Indeed, the global MFA market is projected to grow from $11.1 billion in 2021 to more than $23 billion by 2026.
One of the most common authentication methods in MFA is one-time codes sent to a user through SMS or an authentication app. Unfortunately, these codes can be compromised in several ways. In particular, attackers can:
Instead of intercepting one-time codes, some cybercriminals are exploiting MFA fatigue. The fact is, users are so inundated by MFA prompts that they feel overwhelmed. So, when a hacker tries to log on using their compromised credentials, the user might simply approve the resulting MFA request without stopping to realize that it is not legitimate. As a result, the hacker gets authorized.
There are multiple ways to strengthen your MFA procedures. One is to limit the number of MFA alerts sent to a given user account within a given timeframe, since that can be a sign of malicious access attempts. In addition, educate users to view unexpected MFA alerts with caution. Finally, consider replacing push notifications with other authorization methods that are less vulnerable to hacking.
So, what is the most common cyber-attack? There is no enduring answer to this question, since attack methods fall in and out of popularity. Accordingly, the best strategy for every organization is to adopt a defense-in-depth approach that covers all the functions of the NIST Cybersecurity Framework.
The good news is that the Netwrix suite of solutions does all of this. It empowers you to:
Plus, Netwrix solutions integrate smoothly with many other security tools to streamline processes and enhance cybersecurity.
Ian has over two decades of IT experience, with a focus on data and access governance. As VP of Pre Sales Engineering at Netwrix, he is responsible for ensuring smooth product deployment and identity management integration for customers worldwide, His long career has positioned him to serve the needs of organizations of all sizes, with positions that include running the security architecture team for a Fortune 100 US financial institution and providing security solutions to small and medium businesses.